29. Network Testing Tools
Introduction
This chapter describes the following network testing tools included with TCPware:
|
ARPSNMP |
Keeps track of ARP information and notifies of changes |
|
CHARGEND |
Sends strings of characters, ignoring data received |
|
DAYTIMED |
Sends the current date and time |
|
DISCARD |
Discards any data it receives |
|
ECHOD |
Returns any data it receives |
|
FINGER |
Extracts user information from a remote user information program |
|
IDENT |
Other servers use this to determine the user associated with a connection |
|
NETCU DEBUG |
TCPware's NETCU provides debugging commands |
|
NSLOOKUP |
Verifies DNS name server and host domain information |
|
PEERNAME |
Shows IP address and port information for a connection. |
|
PING |
Verifies that a host on the network is up and reachable |
|
QUOTED |
Checks for TCP connectivity between hosts |
|
TCPDUMP |
Tracks TCP packets over the network |
|
TIME |
Time service |
|
TRACEROUTE |
Tracks TCP routes over the network |
ARPSNMP
ARPSNMP is a program that reads TCPware’s ARP information and keeps track of information that it has seen in ARP.DAT. TCPWARE:ETHERCODES.DAT is used to display information about the manufacturer of the Ethernet address.
To use, create an empty ARP.DAT in your local directory and define the following symbol:
$ arpsnmp :== $tcpware:arpsnmp
Command syntax is as follows:
$ arpsnmp [-d] [-f file_specification]
|
-d |
debug mode: information is displayed to the terminal and not mailed to SYSTEM |
|
-f file_specification |
specifies location for ARP.DAT if it isn’t in the current working directory |
The first time that ARPSNMP is run with an empty ARP.DAT, it reports all ARP entries as new as it adds them to the file, for example:
new station 192.168.0.69 aa:1:2:3:4:5
Each subsequent time that ARPSNMP is run, it compares the ARP table to the contents of ARP.DAT and reports any differences by sending email to the SYSTEM account (unless –d is specified on the command line).
CHARGEND
CHARGEND is the Character Generator Protocol server, defined in RFC 864. It sends strings of characters, ignoring data received, and is a useful debugging tool. CHARGEND can be TCP- or UDP-based. STARTNET starts the service automatically using the TCPWARE:MISC_CONTROL.COM file. The TCPWARE_COMMON:
[TCPWARE.EXAMPLES] directory provides the source code. You can test this service through a TELNET connection to it.
DAYTIMED
DAYTIMED is the Daytime Protocol server, defined in RFC 867. It sends the current date and time as a character string without regard to input. It is a useful debugging and measurement tool. DAYTIMED can be TCP- or UDP-based. STARTNET starts the service automatically using the TCPWARE:MISC_CONTROL.COM file. The TCPWARE_COMMON:[TCPWARE.EXAMPLES] directory provides the source code. You can test this service through a TELNET connection to it.
DISCARD and DISCARDD
DISCARD is the Discard Protocol client and DISCARDD is the Discard Protocol server, defined in RFC 863. It simply throws away any data it receives, and is a useful debugging and measurement tool. It can be TCP- or UDP-based. STARTNET starts the service automatically using the TCPWARE:MISC_CONTROL.COM file. The TCPWARE_COMMON:[TCPWARE.EXAMPLES] directory provides the source code for DISCARD and DISCARDD. You can test the service using a TELNET connection to it.
ECHOD
ECHOD is the Echo Protocol server, defined in RFC 862. It returns any data it receives and is a useful debugging and measurement tool. It can be TCP- or UDP-based. STARTNET starts the service automatically using the TCPWARE:MISC_CONTROL.COM file. You can test this service using a TELNET connection to it.
FINGER and FINGERD
FINGER is the Finger User Information Protocol, defined in RFC 1288. It is used to extract user information from a remote user information program (RUIP). FINGER is TCP-based. STARTNET starts the service automatically using the TCPWARE:MISC_CONTROL.COM file. The TCPWARE_COMMON:[TCPWARE.EXAMPLES] directory provides the source code for FINGERD.
Use FINGER at the DCL level as follows:
$ FINGER user@host
The user is the user to extract information about on the specified host. You must use both parameters.
FINGERD reports the day of the week, hours, and minutes of a login time only if the user has been logged in for LESS than seven days. If the user has been logged on for MORE than seven days, the date in the format dd-mm-yy is reported.
Note! Although
a two-digit year is reported, it is compliant with the year-two-thousand
reporting.
For example:
Old format:
SMITH ZEUS Mary Smith 0 Fri 14:36 FTA419:
New format:
JONES ZEUS John Jones 14 10-Dec-14 FTA372:
IDENT
Other servers use the Identification server (formerly the Authentication Server) to determine the user associated with a connection. The MISC_CONTROL command procedure starts the IDENT server automatically.
NETCU DEBUG
TCPware's Network Control Utility (NETCU) includes DEBUG commands for the IP, TCP, and UDP layers. They display information about IP datagrams, TCP segments, and UDP datagrams sent and received over the network. You can use them to debug network problems.
See the NETCU Command Reference for the DEBUG IP, DEBUG TCP, and DEBUG UDP command descriptions.
NSLOOKUP
The NSLOOKUP utility sends test queries to a DNS name server to test the DNS configuration. You would use NSLOOKUP to find information such as the following for a selected host or domain:
• Default name server
• DNS database records, such as all, A, CNAME, and MX
• All the hosts in a domain
• User processes
The NSLOOKUP utility has two modes, noninteractive and interactive:
|
Noninteractive mode |
Query a host and exit NSLOOKUP |
|
Interactive mode |
Query a host and enter further NSLOOKUP commands |
Setting the mode depends on the syntax you use in entering the NSLOOKUP command. You access noninteractive mode if you use the following syntax at the DCL prompt:
$ nslookup host-to-find [server-to-query]
$
You access interactive mode if you use the following syntax at the DCL prompt:
$ nslookup [- server-to-query]
>
The difference is that noninteractive mode requires at least the host-to-find parameter, while interactive mode is signaled by either the lack of an parameter altogether or a dash preceding the server-to-query parameter. Also, after a noninteractive query, you are back at the DCL prompt, while the interactive query puts you at the > prompt so that you can enter further NSLOOKUP commands.
Both modes allow you to enter options, as described in Setting Options.
Noninteractive Mode
The full noninteractive mode syntax is as follows:
$ nslookup[-option[-option...]]host-to-find [server-to-query]
|
-option |
Sets the state information for a group of lookups. (See Setting Options for details on state information.) You can have multiple options, each prefixed by a dash and separated by a space. |
|
host-to-find |
Hostname or IP address of the host about which to seek information. |
|
server-to-query |
Hostname or IP address of the DNS server to query. You can specify a server only if you also specify a host-to-find. If omitted, TCPware uses the current default server. |
Enter the nslookup command and options in lowercase, but enter the hostname and server name values in their proper case. To interrupt noninteractive mode, use Ctrl/C.
Interactive Mode
The full interactive mode syntax is as follows:
$ nslookup[-option[-option...]] [- server-to-query]
>{ host-to-find | command }
|
-option |
Sets the state information for a group of lookups. (See Setting Options for details on state information.) You can have multiple options, each prefixed by a dash and separated by a space. |
|
- server-to-query |
Hostname or IP address of the DNS server to query. Precede the parameter with a dash and a space. |
|
host-to-find |
Hostname or IP address of the host about which to seek information, as entered at the NSLOOKUP prompt (>). |
|
command |
One of the query commands listed in the section. The command must be less than 256 characters; its case does not matter. |
Enter the nslookup command and options in lowercase, but enter the hostname or server name in its proper case. The nslookup command alone always returns the default server information before presenting the > prompt, at which you can enter either the host-to-find or a command. To interrupt interactive mode, use Ctrl/C. To exit, enter exit or Ctrl/Z.
Entering Host-to-Find Names
You can enter the host-to-find as a hostname or an IP address. If you enter an IP address, the hostname is returned by default.
To look up a host not in the current domain, add a trailing period, such as:
$ nslookup iris.flower.com.
If the trailing period is missing, the default domain name (as determined by the set domain, set srchlist, set defname, or set search commands) is appended.
See the set command description in the Query Command Reference.
Setting Options
NSLOOKUP options set the state information for the particular query. You can set options using the -option parameter, or in interactive mode using the set command. Each option corresponds to a set command keyword.
See the set command description for the keywords that correspond to the options.
For example, the following command uses -option parameters to set the querytype and timeout parameters for the next series of interactive lookups to server AMOS.
$ nslookup -querytype=hinfo -timeout=10 - amos
The alternative would be:
$ nslookup
> set querytype=hinfo
> set timeout=10
>amos
The following command tries to get information about node SIRIUS in domain NENE.COM by querying server ANDY. If unsuccessful, NSLOOKUP tries ten more times and returns to the DCL prompt.
$ nslookup -domain=nene.com -retry=10 sirius andy
Query Command Reference
This section describes the NSLOOKUP query commands accessible at the > prompt. Enter the commands in lowercase or they are considered to be uppercase host-to-find entries.
exit
Exits NSLOOKUP.
Format
>exit
Enter the command in lowercase or it is considered to be hostname "EXIT".
Synonym
>Ctrl/Z
Example
This example displays information about the server and exits NSLOOKUP.
$ nslookup
Default Server: sirius.nene.com
Address: 192.168.95.1
>exit
$
finger
Connects with the FINGER server on the (previously defined) host to display FINGER information. With the optional username parameter, you can focus the lookup on one user.
You can redirect the output from the finger command to a file using the greater-than symbol, as follows:
finger> filename.ext
finger>> filename.ext
The > places the output into filename.ext. The >> appends the output onto file filename.ext. When you direct output to a file, NSLOOKUP prints hash marks after every 50 records received from the server.
Format
>finger[username]
Enter the command in lowercase or it is considered to be hostname "FINGER".
Parameter
username
Focuses the lookup to one username. The username can be case-sensitive.
Example
This example defines the current host as SIRIUS and connects with the FINGER server on SIRIUS to display FINGER information on user GANDALF.
$ nslookup
>sirius
Default Server: sirius.nene.com
Address: 192.168.95.1
Name: sirius.nene.com
Address: 192.168.95.1
>finger gandalf
[sirius.nene.com]
Status of VMScluster on node NENE at 23-JUN-2014 16:52:04.62
Username Node Name New Mail When Terminal
GANDALF SIRIUS Gandalf 3 Mon 08:34 FTA1211:
GANDALF SIRIUS Gandalf 3 Mon 08:34 FTA1212:
help
Displays a brief summary of NSLOOKUP commands.
Format
> help
Enter the command in lowercase or it is considered to be hostname "HELP".
Synonym
>?(question mark)
Example
> ?
NSLOOKUP
COMMAND SUMMARY
(identifiers are shown in uppercase, [] means optional)
Command Meaning
---------------------------------------------------------------------
NAME - print info about the host/domain NAME using default server
NAME1 NAME2 - as above, but use NAME2 as server
ls [opt] DOMAIN [> FILE] - list entities in DOMAIN (optional: output to
FILE)
-a - list canonical names and aliases
-h - list HINFO (CPU type and operating system)
-s - list well-known services
-d - list all records
-t TYPE - list records of the given type (e.g., A,CNAME,MX, etc.)
view FILE - sort an 'ls' output file and view it
help or ? - display this screen
spawn or ! [command] - create child process and execute command
finger [USER] - finger the optional NAME at the current default host
root - set current default server to the root
server NAME - set default server to NAME, using current default server
lserver NAME - set default server to NAME, using initial server
set OPTION - set an option
all - print options, current server and host
[no]defname - append domain name to each query
[no]recurse - ask for recursive answer to query
[no]vc - always use a virtual circuit
domain=NAME - set default domain name to NAME
srchlist=N1[/N2/.../N6] - set domain to N1 and search list to N1,N2, etc.
root=NAME - set root server to NAME
retry=X - set number of retries to X
timeout=X - set initial time-out interval to X seconds
querytype=X - set query type, e.g., A,ANY,CNAME,HINFO,MX,NS,PTR,SOA,WKS
type=X - synonym for querytype
class=X - set query class to one of IN (Internet), CHAOS, HESIOD or ANY
[no]debug - print debugging information
[no]d2 - print exhaustive debugging information
exit - exit the program, ^Z also exits
ls
Lists the information for a domain. The default output contains host names and their Internet addresses.
You can redirect the output from the ls command to a file as follows:
ls...>
filename.ext
ls ...>> filename.ext
The > places the output into filename.ext. The >> appends the output onto file filename.ext. When you direct output to a file, NSLOOKUP prints hash marks after every 50 records received from the server.
Format
>ls[-option [-option...]] domain
Enter the command in lowercase or it is considered to be hostname "LS".
Parameters
-option
See the Options that follow for a list of available options. Always precede an option with a hyphen. Separate multiple options with spaces.
domain
Domain for which to list information.
Options
-a
Lists aliases of hosts in the domain.Synonym for ls -t CNAME.
-d
Lists all records for the domain.Synonym for ls -t ANY.
-h
Lists CPU and operating system information for the domain.Synonym for ls -t HINFO.
-s
Lists well-known services of hosts in the domain.Synonym for ls -t WKS.
-t [type]
Lists all records of the type specified by the set type command, as in Record Types (-t .
|
Value... |
Means... |
|
any |
All records for the domain |
|
a |
Host internet address |
|
afsdb |
AFS database |
|
axfr |
Zone transfer |
|
cname |
Canonical name for an alias |
|
hinfo |
Host CPU and operating system type |
|
isdn |
ISDN information |
|
mb |
Mailbox |
|
mg |
Mail group |
|
minfo |
Mail information |
|
mr |
Mailbox rename |
|
mx |
Mail exchanger |
|
ns |
Name server for the named zone |
|
ptr |
Host name if query is Internet address, otherwise pointer to other information |
|
rp |
Responsible person |
|
rt |
Route through binding |
|
soa |
Domain "start-of-authority" information |
|
txt |
Text information |
|
uinfo |
User information |
|
wks |
Supported well-known services |
|
x25 |
X.25 information |
Examples
1 This example lists information for domain SIRIUS:
>ls nene.com
[sirius.nene.com]
nene.com. server = sirius.nene.com
sirius 192.168.95.1
nene.com. server = nic.near.net
nic.near.net. 192.52.71.4
2 This example lists all records for domain SIRIUS:
>ls -d nene.com
[sirius.nene.com]
nene.com. SOA sirius.nene.com leary.sirius.nene.com
.(76 86400 1800 3600000 86400)
nene.com. NS sirius.nene.com
3 This example appends the output in Example 2 onto an existing FOOBAR.TXT file:
>ls -d nene.com
>> foobar.txt
[sirius.nene.com]
###
Received 165 records.
>
root
Changes the default server to the domain namespace root server.
The default host is a.root-servers.net.
You can change the name of the root server with the set root command.
Format
>root
Enter the command in lowercase or it is considered to be hostname "ROOT".
Synonym
>lserver a.root-servers.net
Example
This example lists the root server name and address.
>root
Default Server: a.root-servers.net
Address: 198.41.0.4
server
lserver
Changes the default server to the specified host:
• The server command uses the current default server to look up information about the host.
• The lserver command uses the initial server to look up information about the host.
If NSLOOKUP cannot find an authoritative answer, it returns the names of servers that might have the answer.
Format
>serverhost
> lserver host
Enter the command in lowercase or it is considered to be hostname "SERVER" or "LSERVER".
Parameter
host
Domain name of the host.
Examples
1 This example changes the default server to GEMMA.
>server gemma
Default Server: gemma.nene.com
Served by:
- NIC.NEAR.NET
192.52.71.4
NENE.COM
- BU.EDU
128.197.27.7
NENE.COM
2 This example changes the default server back to sirius.
>lserver sirius
Default Server: sirius.nene.com
Address: 192.168.95.1
set
Changes state information that affects the lookups.
Format
> set option
Enter the command in lowercase or it is considered to be hostname "SET".
The options are listed as under the Options heading. The abbreviated form of the option is underlined.
Synonym
$ nslookup -option [-option...]
Options
all
Prints the current value of all keyword options and information about the current default server and host.
class=value
Changes the query class to one of the values in Table 32-2. The class specifies the protocol group of the information. The abbreviation is cl.
|
Table 32-2 set class Values |
|
|
Value |
Description |
|
in |
Internet class (default value) |
|
chaos |
Chaos class |
|
hesiod |
MIT Athena Hesiod class |
|
any |
Wildcard for any of the above |
debug
nodebug (default)
Turns debug mode on (debug). Debug provides information about the packet sent to the server and the resulting answer.
d2
nod2 (default)
Turns exhaustive debug mode on (d2), which essentially displays all fields of every packet. If you turn exhaustive debug mode off again (nod2) , you remain in debug mode (see debug).
defname (default)
nodefname
Appends (defname) the default domain name to every single-component lookup, or disables this function (nodefname). You should probably leave the append function on in most cases.
domain=name(default=local domain)
Changes the default domain name to name and appends the default domain name to a lookup request, if defname and searchare set. The domain search list contains the parents of the default domain if it has at least two components in its name.
ignoretc
noignoretc (default)
Ignores packet truncation errors (ignoretc) on output, or disables this function (noignoretc). In most cases, you would want to display these errors.
port=number
Changes the default TCP/UDP name server port to number.
querytype=value
Changes the type of information returned by a query to one of the values in Table 32-3. The default value is a. The synonym is type.
|
Value |
Description |
|
any |
All records for the domain |
|
a |
Host internet address |
|
afsdb |
AFS database |
|
axfr |
Zone transfer |
|
cname |
Canonical name for an alias |
|
hinfo |
Host CPU and operating system type |
|
isdn |
ISDN information |
|
mb |
Mailbox |
|
mg |
Mail group |
|
minfo |
Mail information |
|
mr |
Mailbox rename |
|
mx |
Mail exchanger |
|
ns |
Name server for the named zone |
|
ptr |
Host name if query is Internet address, otherwise pointer to other information |
|
rp |
Responsible person |
|
rt |
Route through binding |
|
soa |
Domain "start-of-authority" information |
|
txt |
Text information |
|
uinfo |
User information |
|
wks |
Supported well-known services |
|
x25 |
X.25 information |
retry=number(default=2)
Sets the number of retries to number. If NSLOOKUP does not receive a reply to a request within the amount of time specified by set timeout, it resends the request. The retry value controls how many times NSLOOKUP resends a request before giving up.
root=host(default=a.root.servers.net)
Changes the name of the root server to host. This changes the default root server when using the root command.
recurse(default)
norecurse
The name server recursively queries other servers if it does not have the information (recurse), or does not do this (norecurse). You would normally want recursive queries.
search
(default)
nosearch
Searches for each name in parent domains of the current domain (search), or disables this function (nosearch). If the lookup request contains at least one period but does not end with a trailing period, search appends the domain names in the domain search list to the request until the server returns an answer.
srchlist=name1 [ /name2 /... /name6 ] (default=local domain)
Sets up a search list by changing the default domain name to name1 and the domain search list to name1, name2, and so on, up to six names, each separated by a slash (/). This command overrides the default domain name and search list of the set domain command.
timeout=interval (default=10)
Changes the timeout interval NSLOOKUP uses while waiting for a reply to the interval number of seconds. (See also retry.)
type=value
See querytype.
vc
novc(default)
Uses a TCP virtual circuit when sending requests to the server (vc), or uses UDP or allows NSLOOKUP to determine whether to use a virtual circuit based on the size of the request (novc). You would normally use novc.
Examples
1 This example sets the search list to NENE.COM and COM.
>set srchl=nene.com/com
2 This example sets the query type to ANY. When listing the host, all records appear.
>set q=any
>sirius
Server: sirius.nene.com
Address: 192.168.95.1
sirius.nene.com
internet address = 192.168.95.1
sirius.nene.com CPU = VAXstation 4000-90 OS = VMS V5.5-2
SET SRCHL=NENE.COM/COMP.PROTOCOLS.SMTP
spawn
Spawns a subprocess in order to execute a DCL command.
Note! You cannot SPAWN with CAPTIVE accounts.
Format
> spawn [command]
Enter the command in lowercase or it is considered to be hostname "SPAWN".
Synonym
> ! [command]
Parameter
command
Command to execute. If omitted, TCPware starts a DCL subprocess.
view
Sorts and lists previous ls command output redirected to a filename.
Format
> view filename
Enter the command in lowercase or it is considered to be hostname "VIEW".
Parameter
filename
Filename to which you redirected output during an ls command.
Example
This example redirects a listing output to the FOOBAR.TXT file, and views the contents of the file.
>ls sirius > foobar.txt
[sirius.nene.com]
###
Received 165 records.
>view foobar.txt
[sirius.nene.com]
nene.com. server = sirius.nene.com
sirius 192.168.95.1
nene.com. server = nic.near.net
nic.near.net. 192.52.71.4
NSLOOKUP Utility Error Messages
If the lookup request was not successful, NSLOOKUP prints an error message. Valid error messages are:
|
Timed-out |
The server did not respond to a request after the amount of time specified in timeout and the number of retries specified in retry. |
|
Non-existent domain |
The host or domain name does not exist. |
|
No response from server |
The server machine does not run a name server. |
|
No records |
The server does not have resource records of the currently specified query type for the host, although the host name is valid. |
|
Connection Refused or Network Is Unreachable |
NSLOOKUP could not make a connection to the name or finger server. Common error with finger and ls requests. |
|
Server failure |
The name server found an internal inconsistency in its database and could not return a valid answer. |
|
Refused |
The name server refused to service the request. |
|
Format error |
The name server found that the request packet was not in the proper format. |
PEERNAME
PEERNAME is a utility that displays the local and remote IP addresses and ports for a given connection. PEERNAME can handle all kinds of network devices: INET, TCP, or BG.
To use, define the following symbol:
$ peername :== $tcpware:peername
Command syntax is as follows:
$ peername network-device
For example, if you have used TELNET to log into a system, you can use PEERNAME to obtain information about that connection:
$ peername TT:
Local address: 192.168.0.69, port: 23
Remote address: 192.168.0.119, port: 21895
PING
The PING utility tells you whether a host is up and whether you can reach it. You have a choice of two PING versions, PING, and PING_V2. The two version are slightly different, with PING displaying a bit more information. PING_V2 originated in TCPware Version 2.
The PING utility uses the ICMP echo and echo reply messages. To use the PING utility, you need BYPASS or SYSPRV privilege. Also, always run the PING utility from an account that has NETMBX privileges.
Note! TCPware limits PINGs to about 64,512 bytes.
Using the Newer PING
Before using the newer version of the PING utility, enter the following:
$ PING :== $TCPWARE:PING
To "ping" a host, enter:
$ PING [-rv] host [data-size [npackets]]
• ·-r – Do not route: do not use another gateway to reach the destination; the destination must be on a local network
• -v – Verbose mode, which displays information on an invalid response
• host – Hostname or internet address of the host to "ping"
• data-size – Size, in bytes, of the ICMP echo data
• npackets – Number of packets to send; if omitted, PING sends an infinite number of packets
To terminate or interrupt PING, enter Ctrl/C.
Example 32-1 shows a PING command and the resulting output. The Ctrl/C appears because the user interrupted the output with Ctrl/C.
NETCU> PING process-gw
PING process-gw.nene.com (192.168.95.126): 56 data bytes
64 bytes from 192.168.95.126: icmp_seq=0. time=10.ms
64 bytes from 192.168.95.126: icmp_seq=1. time=0.ms
64 bytes from 192.168.95.126: icmp_seq=2. time=0.ms
64 bytes from 192.168.95.126: icmp_seq=3. time=0.ms
Ctrl/C
----process-gw.nene.com PING Statistics----
4 packets transmitted, 4 packets received, 0% packet loss
round-trip (ms) min/avg/max = 0/2/10
$
Using PING_V2
PING_V2 is from TCPware Version 2. Before using PING_V2, enter the following:
$ PING :==
$TCPWARE:PING_V2
To "ping" a host using PING_V2, enter:
$ PING host [timeout [data-size [interval [display]]]]
|
host |
Hostname or internet address of the host to "ping" |
|
timeout |
Command timeout time, in seconds (the default is 20 seconds) |
|
data-size |
Size, in bytes, of the ICMP echo data (the default is 128 bytes) |
|
interval |
Interval, in seconds, between the retransmission of the ECHO request if you do not receive a response (the default is 1 second) |
|
display |
Y to enable or N to disable the display of the packets (the default is N) |
If the host responds, a message appears indicating that the host is alive. If the host fails to respond within the allowed time, a message appears indicating that the host did not answer. The number of packets sent, number of invalid packets received (other ICMP packets that were not responses to the ECHO request), and the elapsed time also appear.
PING also returns a status code so that you can use command procedures to test whether various hosts are available. Example 32-2 shows a PING_V2command and the resulting output.
PING process-gw
process-gw is alive
1 echo message sent (0 invalid responses) in 0.01 seconds.
QUOTED
The Quote-of-the-Day service (QUOTED) is a useful tool to check for connectivity. QUOTED is a TCP-based character generator service. As implemented, the QUOTED server listens for TCP connections on TCP port 17. Once you establish a connection, the service sends a short message. The service then throws away any data it receives and closes the connection.
It is your responsibility to provide the quote and define the TCPWARE_QUOTE logical.
There is no specific syntax for the quote. The quote can have a total of 512 characters and is limited to the following characters:
• ASCII printable
• Space
• Carriage return
• Line feed
You need to define a system logical, TCPWARE_QUOTE to specify the quote for the server. The TCPWARE_QUOTE logical name can be either a string or a filename that includes the quote text. Prefix a filename with the @ sign and enclose the definition or filename in quotation marks.
You need SYSNAM or SYSPRV privileges to define the system-wide logical. The following examples show three different ways to define the TCPWARE_QUOTE logical:
$ DEFINE/SYSTEM/EXEC
TCPWARE_QUOTE "Quote-of-the-day"
$ DEFINE/SYSTEM/EXEC TCPWARE_QUOTE "@SYS$MANAGER:QUOTE.TXT"
$ DEFINE/SYSTEM/EXEC TCPWARE_QUOTE "Today's quote is",-
_$ "@SYS$MANAGER:QUOTE.TXT"
To test QUOTED, TELNET to the host that has a defined quote-of-the-day, as follows:
TELNET host QUOTEOR TELNET host 17
(Specifying QUOTE or 17 is identical since the QUOTE server port number is 17.)
For example, the following command does a TELNET operation to BARTLETT's quote-of-the-day server:
$ TELNET BARTLETT QUOTE
The system displays:
%TCPWARE_TELNET-I-TRYING, trying BARTLETT,quote
(192.168.5.75,17) ...
%TCPWARE_TELNET-I-ESCCHR, escape (attention) character is "^
"Quote-of-the-day"
If the system logical is not defined, the system displays:
%TCPWARE_TELNET-I-TRYING, trying BARTLETT,quote
(192.168.5.75,17) ...
%TCPWARE_TELNET-I-ESCCHR, escape (attention) character is "^
No quote-of-the-day is currently defined.
TCPDUMP
TCPDUMP is a useful mechanism for tracking TCP packets by displaying information in the packet headers. You can specify the type of packet information to extract by including the relevant options and expressions.
Use of TCPDUMP assumes a thorough understanding of the TCP protocol.
Before using TCPDUMP, enter the following foreign command definition:
$ TCPDUMP:==$TCPWARE:TCPDUMP
The TCPDUMP command syntax is as follows:
$ TCPDUMP [options] [expressions]
You can also use the TCPDUMP command on the Network Control Utility (NETCU) level. This allows you to use OpenVMS qualifiers in place of (or in addition to) UNIX-style options. To use TCPDUMP on the NETCU level, enter the following:
$ NETCU TCPDUMP [qualifiers | options] [expressions]
For complete details on the available options and expressions, see TCPDUMP Command Reference later in this chapter.
Interpreting TCPDUMP Output
Much of the information that follows is adapted from material provided by the Lawrence Berkeley Laboratory, University of California, Berkeley, and must contain the following notice:
Copyright (c) 1988, 1989, 1990, 1991, 1992, 1993, 1994, 1995, 1996
The Regents of the University of California. All rights reserved.
"This product includes software developed by the University of California, Lawrence Berkeley Laboratory and its contributors."
The output of TCPDUMP is protocol-dependent. The following gives a brief description and examples of most of the various output formats. The description assumes familiarity with RFC 793, Transmission Control Protocol.
Monitoring TCP Packets
Consider the command and its output in TCPDUMP Output .
$ tcpdump host bart
Getting stats.
tcpdump: listening on ESA0:
18:21:59.000400 bart.nene.com.1023 > marge.login: S
560913442:560913442(0) win 24576 <mss 1460,wscale 0,eol> (DF)
18:21:59.004000 bart.nene.com.1023 > marge.login: . ack 513152385
win 24576 (DF)
18:21:59.004100 bart.nene.com.1023 > marge.login: P 0:1(1) ack 1 win 24576
(DF)
The general format of a TCP protocol line is as follows, with references to TCPDUMP Output in the explanations given in parentheses:
timestamp src>dst: flags [
first-byte:last-byte (total-bytes) ack seqno
win bytes urg <options>]
|
timestamp ( 18:21:59.000400) |
By default, all output lines are preceded by a time stamp, the current clock time in the form hours:minutes:seconds.decimal. The time stamp reflects the time the driver delivers the packet. No attempt is made to account for the time lag between when the Ethernet interface removed the packet from the wire and when the driver services the I/O request. The additional -tt option you can use with the TCPDUMP command displays an unformatted time stamp, while the -t option removes the time stamp altogether. |
|
src>dst: (bart.nene.com.1023 > marge.login:) |
Source and destination IP address and port. |
|
flags
– S (SYN), F (FIN), P (PUSH), |
Transition flags that can appear in combination. |
|
first-byte:last-byte (total-bytes) (560913442:560913442(0)) |
Packet data sequence number, the first byte followed by the last byte of data, and the total bytes. |
|
ack seqno (ack 513152385) |
Sequence number of the next data expected in the other direction on this connection. |
|
win bytes (win 24576) |
Number of bytes of receive buffer space available in the other direction on this connection. |
|
urg (not shown) |
The packet contains "Urgent" data. |
|
<options> (not shown) |
TCP options, enclosed in angle brackets (<>). |
|
(DF) (various lines) |
The IP do-not-fragment flag is included with the packet. |
The src and dst values and the flags (S, F, P, R, or .) are always present. The other fields depend on the contents of the packet's TCP protocol header and appear only if appropriate.
Example 32-4 shows the opening portion of an RLOGIN operation from BART to MARGE.
bart.1023 > marge.login: S 768512:768512(0) win 4096
<mss 1024>
marge.login > bart.1023: S 947648:947648(0) ack 768513 win 4096 <mss
1024>
bart.1023 > marge.login: .ack 1 win 4096
bart.1023 > marge.login: P 1:2(1) ack 1 win 4096
marge.login > bart.1023: . ack 2 win 4096
bart.1023 > marge.login: P 2:21(19) ack 1 win 4096
marge.login > bart.1023: P 1:2(1) ack 21 win 4077
marge.login > bart.1023: P 2:3(1) ack 21 win 4077 urg 1
marge.login > bart.1023: P 3:4(1) ack 21 win 4077 urg 1
Here is the explanation for each line in RLOGIN Output :
• bart.1023 > marge.login: S 768512:768512(0) win 4096 <mss 1024>
TCP port 1023 on BART sends a packet to port LOGIN on MARGE. The S indicates that the SYN flag was set. The packet sequence number is 768512 and it contains no data. There is no piggybacked ACK, the available receive window is 4096 bytes, and there is a maximum segment size (MSS) option requesting an MSS of 1024 bytes.
• marge.login > bart.1023: S 947648:947648(0) ack 768513 win 4096 <mss 1024>
MARGE replies with a similar packet except that it includes a piggy-backed ACK in response to BART's SYN.
• bart.1023 > marge.login: . ack 1 win 4096
BART then sends an ACK in response to MARGE's SYN. The .means that no flags were set. The packet contains no data, so there is no data sequence number. Note that the ACK sequence number is a small integer (1). The first time TCPDUMP sees a TCP "conversation," it displays the sequence number from the packet.
• bart.1023 > marge.login: P 1:2(1) ack 1 win 4096
marge.login > bart.1023: .ack 2 win 4096
On subsequent packets of the conversation, the difference between the current packet's sequence number and this initial sequence number is displayed. This means that sequence numbers after the initial one can be interpreted as relative byte positions in the conversation's data stream (with the first data byte in each direction being 1). (The -s option would override this feature, causing the original sequence numbers to be output.)
• bart.1023 > marge.login: P 2:21(19) ack 1 win 4096
BART sends MARGE 19 bytes of data (bytes 2 through 20 in the BART-to-MARGE side of the conversation). The P (PUSH) flag is set in the packet.
• marge.login > bart.1023: P 1:2(1) ack 21 win 4077
MARGE indicates that it received data up to, but not including, byte 21. Most of this data is apparently sitting in the socket buffer, since MARGE's receive window decreased by 19 bytes. MARGE also sends one byte of data to BART in this packet.
• marge.login > bart.1023: P 2:3(1) ack 21 win 4077 urg 1
marge.login > bart.1023: P 3:4(1) ack 21 win 4077 urg 1
MARGE sends two bytes of urgent, pushed data to BART.
Monitoring UDP Packets
The UDP format is illustrated by this rwho packet:
molly.who > broadcast.who: udp 84
This says that port WHO on host MOLLY sent a UDP datagram to port WHO on host BROADCAST, the Internet broadcast address. The packet contained 84 bytes of user data.
Some UDP services are recognized (from the source or destination port number) and the higher level protocol information is displayed; in particular, Domain Name System (DNS) service requests and Sun Remote Procedure Calls to the Network File System (NFS).
Displaying Link Level Headers
The -e option of the TCPDUMP command displays the link level header of each dump line. On Ethernet systems, this displays the source and destination addresses, protocol, and packet length. For example, the following command displays the additional information shown in bold type:
$ tcpdump -e host bart -t
Getting stats.
tcpdump: listening on ESA0:
aa:0:4:0:3a:8 aa:0:4:0:15:a ip 62: bart.nene.com.1023 > marge.login:
S
176494692:176494692(0) win 24576 <mss 1460,wscale 0,eol> (DF)
aa:0:4:0:3a:8 aa:0:4:0:15:a ip 60: bart.nene.com.1023 > marge.login:
. ack
128739885 win 24576 (DF)
aa:0:4:0:3a:8 aa:0:4:0:15:a ip 60: bart.nene.com.1023 > marge.login:
P
0:1(1) ack 1 win 24576 (DF)
The link level headers begin with aa. (Note that time stamps were omitted since the -t option was used.)
On FDDI networks, the -e option displays the frame control field – the source and destination addresses, and the packet length – that governs the interpretation of the rest of the packet.
Normal packets (such as those containing IP datagrams) are asynchronous, with a priority value between 0 and 7; for example, async4. Such packets are assumed to contain an 802.2 Logical Link Control (LLC) packet; the LLC header is displayed if it is not an ISO datagram or so-called Subnetwork Access Protocol (SNAP) packet.
Monitoring ARP and RARP Packets
The following description assumes familiarity with the ARP and RARP protocols. See Chapter 6, Common Interfaces, the Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP) subsections for further information.
Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP) output shows the type of request and its arguments.
The format is intended to be self-explanatory. The following abbreviated sample output is taken from the start of an RLOGIN operation from host MARGE to BART:
$ tcpdump host bart
-t
arp who-has bart.humor.com tell marge.nene.com
arp reply bart.nene.com is-at aa:0:4:0:1f:8
The first line indicates that MARGE sent an ARP packet asking for BART's Ethernet address. BART replied with its Ethernet address, aa:0:4:0:1f:8.
You can also specify not to convert IP addresses to hostnames by using the -n option:
$ tcpdump host bart
-t -n
arp who-has 128.3.254.6 tell 128.3.254.68
arp reply 128.3.254.6 is-at aa:0:4:0:1f:8
With the additional link level header information, the output would be as follows:
$ tcpdump host bart
-t -e
aa:0:4:0:1:8 aa:0:4:0:15:a ip 82: arp who-has 128.3.254.6 tell
128.3.254.68
aa:0:4:0:1:8 aa:0:4:0:15:a ip 82: arp reply 128.3.254.6 is-at aa:0:4:0:1f:8
DNS Name Server Requests
The following description assumes familiarity with the DNS protocol. See Chapter 3, Domain Name Services, for further information.
Domain Name System (DNS) name server requests are formatted as:
src>dst: qidop? flagsqtypeqclassname (len)
Figure 32-1 shows an example in which APOLLO queries the domain server on BART for an address (type A) record associated with the name MARGE.NENE.COM.
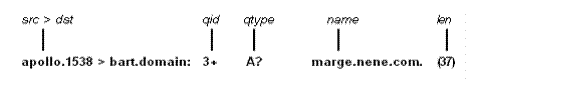
• The source and destination hosts (src >dst) are given.
• The query id (qid) is 3 (the + indicates that the "recursion desired" flag was set).
• The query operation (op?) is omitted since it is the normal one, Query. If op had been anything else, it would appear between the 3 and the +.
• The query type (qtype) is A for Address record.
• The qclass is omitted since it is the normal one, C_IN. Any other qclass would have been displayed immediately after the A.
• The name is the domain name of target host MARGE.
• The query length (len) is 37 bytes, not including the UDP and IP protocol headers.
A few anomalies are checked and can result in extra fields enclosed in square brackets. If a query contains an answer, name server, or authority section, ancount, nscount, or arcount are displayed as [na], [nn], or [nau], where n is the appropriate count. If any of the response bits are set (AA, RA, or rcode) or any of the "must be zero" bits are set in bytes two and three, [b2&3=x] is displayed, where x is the hex value of header bytes two and three.
DNS Name Server Responses
DNS name server responses are formatted as:
src> dst: qid op rcode flags a/n/au qtype qclass data (len)
Figure 32-2 shows two examples.
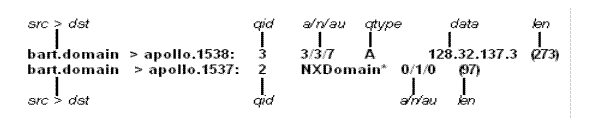
In the first example, BART responds to query 3 from APOLLO with three answer records (a), three name server records (n), and seven authority records (au). The first answer record is type A (address) and its data is internet address 128.32.137.3. The total size of the response is 273 bytes, excluding UDP and IP headers. The op (Query) and rcode (NoError) were omitted, as was the class (C_IN) of the A record.
In the second example, BART responds to query 2 with a response code of nonexistent domain (NXDomain) with no answers, one name server, and no authority records. The * indicates that the authoritative answer bit was set. Since there were no answers, there is no qtype, qclass, or data displayed.
Other flag characters that might appear are - (recursion available, RA, not set) and | (truncated message, TC, set). If the "question" section does not contain exactly one entry, [nq] is displayed.
Note that name server requests and responses tend to be large, and the default snapshot length of 68 bytes may not capture enough of the packet to display. Use the -s flag to increase the snapshot length if you need to seriously investigate name server traffic (-s 128 is known to be effective).
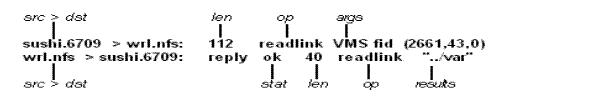
NFS Requests and Replies
The following description assumes familiarity with the Network File System (NFS). See Chapter 13, NFS-OpenVMS Client Management, or Chapter 14, NFS-OpenVMS Server Management, for further information.
NFS requests and replies are displayed as:
src.xid>dst.nfs: len op
args
src.nfs >dst.xid: reply statlenopresults
Figure 32-3 shows an example. SUSHI sends a transaction with id 6709 to WRL (note that the number following the src host is the transaction ID, not the source port). The request was 112 bytes long, excluding the UDP and IP headers. The operation was a readlink (read symbolic link) on file handle (VMS fid) 2661,43,0. Host WRL replies ok with the contents of the link.
If you use the -v (verbose) option, additional information is displayed. For example:
sushi.1372a > wrl.nfs: 148 read VMS fid (2661,43,0)
8192 bytes @ 24576
wrl.nfs > sushi.1372a: reply ok 1472 read REG 100664 ids 417/0 sz 29388
In the first line, SUSHI queries WRL to read 8192 bytes from file handle 2661,43,0 at byte offset @24576. WRL responds with ok. The packet shown on the second line is the first fragment of the reply, and hence is only 1472 bytes long. (The other bytes follow in subsequent fragments, but these fragments do not have NFS or even UDP headers and so might not be displayed, depending on the filter expression used.)
Because of the -v option, some of the file attributes returned in addition to the file data are displayed: the file type (REG, for regular file), the file mode (in octal, 100664), the UID and GID (417/0), and the file size (sz, 29388) . (The -v option also displays the IP header TTL, ID, and fragmentation fields, which were omitted from this example.) If you use -v more than once, even more details are displayed.
Note that NFS requests are very large and much of the detail is not displayed unless the snapshot length is increased. Try using -s 192 to watch NFS traffic.
NFS reply packets do not explicitly identify the RPC operation. Instead, TCPDUMP keeps track of "recent'' requests, and matches them to the responses using the transaction ID. If a response does not closely follow the corresponding request, it might be ignored.
TCPDUMP supports the following options/qualifiers enabling more decoding of RPC-based services.
R_RPC
-”R” all|udp|tcp
/RPC [=ALL|UDP|TCP]
For a UNIX-style option, the “R” must be uppercase and quoted.
The option/qualifier values are:
• ALL (default) decodes both UDP and TCP
• UDP decodes UDP only
• TCP decodes TCP only.
The following RPC protocols are decoded:
• For NFS:
– Network Lock Manager (v.1)
– Net Status
– PCNFS (v.1)
• For Portmapper:
– Network Lock Manager (v.3)
– Mount
– PCNFS (v.2)
The display with /RPC=qualifier used will look like this:
To display more detail, increase the size of snapshot_size using the /SNAP
option.
$ netcu tcpdump /rpc=all /snap=8192 host flintstone
Tcpdump: listening on IPA0:
16:59:54.165987 test.bedrock.com60e19a3d > construction.bedrock.com.NFS:
udp(AUTH_UNIX: Machine=drilling.bedrock.com,Uid=1111,Gid=22)
GETATTR(Fh=6070000.1000000.a00.2a8a 0200)
16:59:54.169893 test.bedrock.com.NFS >
test.bedrock.com.60e19a3d:
udp GETATTR = OK,Type=DIR,Mode=040755,Nlink=3,Uid=1111,Gid=2,Size=3584,
Rdev=ffffa5a8,Blocks=8,Fsid=706,fileID=166442
IP Fragmentation
Fragmented Internet datagrams are displayed as:
(fragid:size@offset+)
(fragid:size@offset)
The first form, which includes the ending +, indicates that there are more fragments. The second form indicates the last fragment. The id parameter is the fragment ID, size is the fragment size (in bytes) excluding the IP header, and offset is this fragment's offset (in bytes) in the original datagram.
Information is displayed for each fragment. The first fragment contains the higher level protocol header and the fragment information is displayed after the protocol information. Fragments after the first contain no higher level protocol header, and the fragment information is displayed after the source and destination addresses. For example, here is part of an FTP from NENE.EDU to LBL-BART.ARPA over a CSNET connection that does not appear to handle 576-byte datagrams:
nene.ftp-data> bart.1170: . 1024:1332(308) ack 1 win
4096 (frag 595a:328@0+)
nene > bart: (frag 595a:204@328)
bart.1170 > nene.ftp-data: . ack 1536 win 2560
• Addresses in the third line do not include port numbers, because the TCP protocol information is all in the first fragment, and it is not know what the port or sequence numbers will be when the later fragments are displayed.
• The TCP sequence information in the first line is displayed as if there were 308 bytes of user data when, in fact, there are 512 bytes (308 in the first fragment and 204 in the second). If you are looking for holes in the sequence space or trying to match up ACKs with packets, this can be misleading.
A packet with the IP do-not-fragment flag is marked with a trailing (DF).
TCPDUMP Command Reference
This section shows the format for and examples of the TCPDUMP command.
The first form of the TCPDUMP command is available on the DCL level as:
$ TCPDUMP:==$TCPWARE:TCPDUMP
$ TCPDUMP [options] [expressions]
The second form is on the Network Control Utility (NETCU) level. This form allows you to use OpenVMS qualifiers in place of (or in addition to) UNIX-style options. To use TCPDUMP on the NETCU level, enter the following:
$ NETCU TCPDUMP [qualifiers | options] [expressions]
The options and their qualifier equivalents are listed together.
TCPDUMP
TCPDUMP displays the headers of packets on a network interface that match the boolean expression. The OpenVMS implementation currently works only with HP-compatible Ethernet cards. Some of the command line switches were changed from the UNIX version to support OpenVMS's case-insensitive command line.
PHY_IO privilege is required to use TCPDUMP, unless reading packets from a file. If using the TCPware drivers for packet capturing, LOG_IO and SYSPRV or BYPASS privileges are also needed.
Format
TCPDUMP [ options | qualifiers] [expressions]
Options and Qualifiers
Note! Only options are available if using TCPDUMP as a foreign command at the DCL prompt. You can mix and match options and qualifiers if using TCPDUMP as a NETCU command. In each case, the option is listed before its equivalent qualifier.
-a
/NO_RELATIVE_SEQUENCE_NUMBERS
Displays absolute, rather than relative, TCP sequence numbers. /RELATIVE is the default.
-b bufcount
/BUFFERS=bufcount
Sets the number of receive buffers for the Ethernet adapter to bufcount. The default is 255 on VAX, 175 on AXP and I64. You may need to lower the number if you receive the message %SYSTEM-F-EXQUOTA, process quota exceeded. This option does not apply to the TCPware drivers. Valid values are 1 to 255.
-c exitcount
/COUNT=exitcount
Exits after receiving exitcount packets.
-d
/HOSTNAMES=NOQUALIFIED
/NODOMAINS
Does not display host names as fully qualified domain names. For example, display nic instead of nic.ddn.mil. /HOSTNAMES=QUALIFIED is the default.
-e
/LINK_HEADERS
/ETHERNET_HEADER
Displays the link-level header on each dump line. (See Displaying Link Level Headers .)
-f
/HOSTNAMES=NOFOREIGN
/FOREIGN_NUMERICALLY
Displays "foreign" internet addresses numerically, not symbolically. FOREIGN is the default.
-g
/NETWORK
Translates network and broadcast addresses to domain names.
-i interface
/INTERFACE=interface
Listens on the interface interface. If unspecified, TCPDUMP searches for a configured interface (excluding loopback). Supported interfaces appear in Table 32-4.
|
Device... |
Which is... |
On platform... |
For medium... |
|
UVA-0 |
DELUA, DEUNA |
VAX, AXP |
Ethernet |
|
QNA-0 |
DEQNA, DELQA, DEQTA |
VAX, AXP |
Ethernet |
|
BNA-0 |
DEBNA, DEBNI |
VAX, AXP |
Ethernet |
|
SVA-0 |
DESVA |
VAX, AXP |
Ethernet |
|
MNA-0 |
DEMNA |
VAX, AXP |
Ethernet |
|
ISA-0 |
SGEC, TGEC |
VAX, AXP |
Ethernet |
|
MXE-0 |
PMAD |
VAX, AXP |
Ethernet |
|
ERA-0 |
DE422, DE425 |
AXP |
Ethernet |
|
EIA-0 |
DE602, i82558 |
AXP, IA64 |
Ethernet |
|
EWA-0 |
TULIP, DEGXX |
AXP, IA64 |
Ethernet |
|
MFA-0 |
DEMFA |
VAX, AXP |
FDDI |
|
FZA-0 |
DEFZA, DEFTA |
VAX, AXP |
FDDI |
|
FAA-0 |
DEFAA |
VAX, AXP |
FDDI |
|
FEA-0 |
DEFEA |
AXP |
FDDI |
|
FQA-0 |
DEFQA |
VAX, AXP |
FDDI |
|
FPA-0 |
DEFPA |
AXP |
FDDI |
|
IP |
IPDRIVER |
VAX, AXP |
N/A * |
|
UDP |
UDPDRIVER |
VAX, AXP |
N/A * |
|
TCP |
TCPDRIVER |
VAX, AXP |
N/A * |
|
* Because these drivers are device-independent, filter expressions based on portions of the Ethernet header are not valid. Additionally, only packets valid for that particular driver are delivered to TCPDUMP (UDPDRIVER only delivers UDP packets, not TCP or other protocols such as ARP/RARP). When using higher level drivers to capture packets, it is also not necessary to contain the protocol in the filter expression: TCPDUMP -i udp udp and host marge is redundant and results in additional overhead while processing packets. The proper usage would be TCPDUMP -i udp host marge. BOOTP requests are displayed, though with an invalid source address. The advantage of using these drivers is the ability to view your own packets, as well as a decrease in the number of lost packets. |
|||
-j file
/FILTER_EXPRESSIONS=file
Uses the specified file as input for the filter expression. Any additional expressions given on the command line are ignored.
-k packetype
/PACKET_TYPE=packetype
Forces packets selected by the expression to be interpreted by the specified packetype. Currently known types are rpc (Remote Procedure Call), rtp (Real-Time Applications Protocol), rtcp (Real-Time Applications Control Protocol), vat (Visual Audio Tool), and wb (Distributed White Board).
-l
/LINE_BUFFERED
Makes stdout line buffered.
-n
/NOHOSTNAMES
/NUMERICALLY
Does not convert addresses (host addresses, port numbers, and so on) to names. (See Monitoring ARP and RARP Packets for an example.)
-o
/NOOPTIMIZER
Does not run the packet-matching code optimizer. This is useful only if you suspect a bug in the optimizer. The default is /OPTIMIZER.
-q
/SHOW=LESS
/QUIET
Quick output.Displays less protocol information so that output
lines are shorter. The default is
/SHOW=NORMAL.
-r file
/INPUT=file
/READ_BINARY=file
Reads packets from the file created with the -w option.
-”R” all|dup|tcp
/RPC [=ALL | UDP | TCP]
Displays RPC information.
For UNIX-style options the “R” must be uppercase and in quotation marks.
-s snapshotlength
/DATA=snapshotlength
/SNAPSHOT_SIZE=size
Captures snapshotlength bytes of data from each packet, rather than the default of 68 bytes. 68 bytes is adequate for IP, ICMP, TCP, and UDP, but may truncate protocol information from name server and NFS packets. Packets truncated because of a limited snapshot are indicated in the output with [|proto], where proto is the name of the protocol level at which the truncation occurred.
If a snapshot of IP data is smaller than the actual packet size, the message truncated-ip - n bytes missing!appears. This is an informational message, and the data captured may be sufficient. If you need to see more data, use -s (or /DATA) to increase the snapshot length.
Note that taking larger snapshots both increases the amount of time it takes to process packets, and effectively decreases the amount of packet buffering. This can cause packets to be lost. You should limit snapshotlength to the smallest number that captures the protocol information you need.
-t
/TIMESTAMPS=value
/NOTIMESTAMPS
/NOTIME
Causes TCPDUMP to display a timestamp on each output line.
Accepted values are UNIX, DELTA, and RELATIVE. The /NOTIMESTAMPS qualifier
disables the timestamp. The default is
/TIME=FORMAT.
-tt
/TIME=NOFORMAT
Displays an unformatted time stamp on each dump line. The default is /TIME=FORMAT.
-u
/OUTPUT=file
Redirects TCPDUMP output to an ASCII file.
-v
/SHOW=MORE
/VERBOSE
Verbose output. For example, the time-to-live (TTL) and type-of-service (TOS) information in an IP packet is displayed. (See NFS Requests and Replies .)
-vv
/SHOW=FULL
/FULL
"Hyperverbose" output. For example, additional fields are displayed from NFS reply packets.
-w file
/WRITE_BINARY=file
Writes the raw packets to a file, rather than parsing and displaying them out. The file can later be displayed with the -r option.
This file is written in libpcap format. When the interface specified is an Ethernet device the data in the file can be analyzed with Ethereal and similar tools.
-x
/HEXADECIMAL
Displays each packet (minus its link level header) in hexadecimal format. The smaller of the entire packet and snapshotlength byte values are displayed.
-z
/ASCII
Displays each packet in hexadecimal format with the ASCII equivalent.
Expressions
Recall that a TCPDUMP command consists of the following elements:
TCPDUMP [ options | qualifiers] [expressions]
Expressions select which packets to dump. Only packets for which the expression is true are dumped (or all packets if the expression is omitted). An expression breaks down into one or more primitives:
expression = primitive primitive ...
Primitives usually break down into a qualifier and an address:
primitive = qualifier address
Expression Qualifiers
There are three kinds of qualifiers – type, direction, and protocol:
• Type qualifiers define the ID name or number type. Possible types are:
– host (default)
– net
– port
Examples of primitives using these qualifiers are host foo, net 128.3, and port 20. The default is host if the type qualifier is omitted, so that foo and host foo are equivalent. A host can be either an IP address or hostname. A net can either be a name from the TCPWARE:NETWORKS.file, or a network number, and can include the additional mask qualifier.
• Direction qualifiers specify a transfer direction, and are prepended to the type qualifier:
– src
– dst
– src or dst (default)
– src and dst
Examples of primitives using these qualifiers are src foo, dst net 128.3, and src or dst port ftp-data. The default is src or dst if the direction qualifier is omitted, so that port ftp-data is true for a source or destination port.
• Protocol qualifiers restrict the match to a particular protocol, and are prepended to the direction qualifier. Possible protocols are:
– ether
– fddi
– icmp
– ip
– ipx
– arp
– rarp
– decnet
– lat
– sca
– moprc
– mopdl
– tcp
– udp
Examples of primitives using these qualifiers are ether src foo, arp net 128.3, and tcp port 21. If the protocol qualifier is omitted, the default is all protocols consistent with the type. For example:
– src foo implies ip, arp, or rarp
– net bar implies ip, arp, or rarp
– port 53 implies tcp or udp
You can be even more specific about the ip protocol by adding proto and the IP protocols cmp, igrp, dp, nd, or cp; for example, ip proto cmp. (Note that some protocols are preceded by backslashes to distinguish them from protocol qualifiers.) The same goes for the ether protocols p, rp, and arp, such as in ether proto p.
The fddi protocol qualifier is actually an alias for ether, and are treated identically as meaning the data link level used on the specified network interface. FDDI headers contain Ethernet-like source and destination addresses, and often contain Ethernet-like packet types, so you can filter on these FDDI fields just as with the analogous Ethernet fields. (FDDI headers also contain other fields, but you cannot name them explicitly in a filter expression.)
Other Expressions
There are additional special, "primitive" qualifiers that do not follow the pattern:
• gateway
• broadcast
• less
• greater
• arithmetic expressions
All of these are described in the Primitives subsection that follows.
More complex filter expressions are built up by using the words and, or, and not to combine primitives. For example, host foo and not port ftp and not port ftp-data. To save typing, identical qualifier lists can be omitted. For example, the following two expressions are identical, the first being the abbreviated form:
tcp dst port ftp or ftp-data or domain
tcp dst port ftp or tcp dst port ftp-data or tcp dst port domain.
Expression Primitives
dst[host]host
IP destination field of the packet must be host.
src[host]host
IP source field of the packet must be host.
[host]host
IP source or destination of the packet must be host. Any of the above host expressions can be prepended with the keywords ip, arp, or rarp, as in ip host host, which is equivalent to ether proto ip and host host. If host is a name with multiple IP addresses, each address is checked for a match.
ether dst ehost
Ethernet destination address must be ehost, which is either a name from the TCPWARE:ETHERS.file, or a number.
ether srcehost
Ethernet source address must be ehost.
ether[host]ehost
Ethernet source or destination address must be ehost.
gatewayhost
Packet must use host as a gateway; that is, the Ethernet source or destination address was host, but neither the IP source nor destination was host. (This makes the expression equivalent to ether host ehost and not host host.) The host must be a name and must be found in both the TCPWARE:HOSTS.andTCPWARE:ETHERS.files.
dst netnet
IP destination address of the packet must have a network ID of net.
src netnet
IP source address of the packet must have a network ID of net.
netnet
Either the IP source or destination address of the packet must have a network ID of net.
netnetmaskmask
IP address must match its network ID with the specified mask; can be qualified with src or dst.
netnet/length
IP address must match its network ID with the specified mask length, in bits; can be qualified with src or dst.
dst portport
Packet must be IP/TCP or IP/UDP and have a destination port value, a number or name used in the TCPWARE:SERVICES.file. If a name, both the port number and protocol are checked. If a number or ambiguous name, only the port number is checked. For example, dst port 513 displays both TCP/LOGIN and UDP/WHO traffic; dst port domain displays both TCP/DOMAIN and UDP/DOMAIN traffic.
src portport
Packet must have a source port value.
portport
Either the source or destination port of the packet must be port. Any of the above port expressions can be prepended with the keywords tcp or udp, as in tcp src port port, which matches only TCP packets whose source port is port.
lesslength
Packet must have a length less than or equal to length (equivalent to len <= length).
greaterlength
Packet must have a length greater than or equal to length (equivalent to len >= length).
ip protoprotocol
Packet must be an IP packet of protocol type protocol, which can be a number or one of the names cmp, igrp, dp, nd, or cp. Note that tcp, udp, and icmp must be escaped using a backslash (F0>) to distinguish them from qualifiers.
[ether] broadcast
Packet must be an Ethernet broadcast packet. The ether keyword is optional.
ip broadcast
Packet must be an IP broadcast packet. It checks for both the all-zeros and all-ones broadcast conventions, and looks up the local subnet mask.
[ether] multicast
Packet must be an Ethernet multicast packet (shorthand for ether[0] & 1 != 0).
ip multicast
Packet must be an IP multicast packet.
ether protoprotocol
Packet must be of Ethernet type protocol, which can be a number or name like p, rp, or F30@Z7@Lam>rarp. Note that these identifiers must be escaped using a backslash (\).
In the case of FDDI (such as fddi proto arp), the protocol identification comes from the 802.2 Logical Link Control (LLC) header, which is usually layered on top of the FDDI header. TCPDUMP assumes, when filtering on the protocol identifier, that all FDDI packets include an LLC header, and that the LLC header is in so-called Subnetwork Access Protocol (SNAP) format.
decnet srchost
DECNET source address must be host, which can be an address of the form 10.123, or a DECNET hostname.
decnet dsthost
DECNET destination address must be host.
decnet hosthost
Either the DECNET source or destination address must be host.
ip, arp, rarp, decnet
Abbreviation for ether proto protocol for one of these protocols.
ipx{ src | dst } host
With ipx alone, packet must be an IPX packet. With src or dst, the packet must come from or go to an ethernet host.
lat, moprc, mopdl
Abbreviation for ether proto protocol for one of these protocols. Note that TCPDUMP does not currently know how to parse these protocols.
tcp, udp, icmp
Abbreviation for ether proto protocol from one of theseprotocols.
exprrelational-operator expression
The relation must hold, where relational-operator is one of >, <, >=, <=, =, !=, and expression is an arithmetic expression composed of integer constants (expressed in standard C syntax), the normal binary operators (+, -, *, /, &, |), a length operator, and special packet data accessors (see the following subsection).
Accessing Data Within a Packet
To access data inside a packet, use the syntax:
proto[expr : size]
• proto is one of ether, fddi, ip, arp, rarp, tcp, udp, or icmp, and indicates the protocol layer for the index operation.
• expr is the byte offset, relative to the indicated protocol layer.
• size is optional and indicates the number of bytes in the field of interest. It can be either 1, 2, or 4, and defaults to 1. The length operator, indicated by the keyword len, gives the length of the packet.
For example:
• ether[0] & 1 != 0 catches all multicast traffic.
• ip[0] & 0xf != 5 catches all IP packets with options.
• ip[6:2] & 0x1fff = 0 catches only unfragmented datagrams and fragment zero of fragmented datagrams. This check is implicitly applied to the TCP and UDP index operations. For instance, tcp[0] always means the first byte of the TCP header, and never means the first byte of an intervening fragment.
Combining Primitives
You can combine primitives using:
• A parenthesized group of primitives and operators (parentheses must be escaped)
• Negation (! or not) (you must enclose expressions using ! in quotes)
• Concatenation (& or and)
• Alternation (| or or)
Negation has the highest precedence. Alternation and concatenation have equal precedence and associate left to right. Note that explicit and tokens, not juxtaposition, are required for concatenation.
If the identifier omits a qualifier, the most recent qualifier applies. For example,
not host vs and ace is short for not host vs and host ace, which should not be confused with not (host vs or ace).
Expression arguments can be passed to TCPDUMP as either a single argument or as multiple arguments, whichever is more convenient.
Examples
1 These identical examples display all packets arriving at or departing from BART.
$ tcpdump bart
$ tcpdump host bart
2 These identical examples display traffic between HELIOS and either HOT or ACE.
$ tcpdump helios and (hot or ace)
$ tcpdump host helios and (hot or ace)
3 These identical examples display all IP packets between ACE and any host except HELOIS.
$ tcpdump ip ace and not helios
$ tcpdump ip host ace and not helios
4 This example displays all traffic between local hosts and hosts at Berkeley.
$ tcpdump net ucb-ether
5 This example displays all FTP traffic through gateway SNUP (note that the expression is quoted because of the parentheses).
$ tcpdump "gateway snup and (port ftp or ftp-data)"
6 This example displays traffic neither sourced from nor destined for local hosts (if you gateway to one other net, this information should never make it onto your local net).
$ tcpdump ip and not net localnet
7 This example displays the start and end packets (the SYN and FIN packets) of each TCP conversation that involves a nonlocal host.
$ tcpdump "tcp[13] & 3 != 0 and not src and dst net localnet"
8 This example displays IP packets longer than 576 bytes sent through gateway HOMER.
$ tcpdump "gateway homer and ip[2:2] > 576"
9 This example displays IP broadcast or multicast packets not sent over Ethernet broadcast or multicast.
$ tcpdump "ether[0] & 1 = 0 and ip[16] >= 224"
10 This example displays all ICMP packets that are not echo requests/replies (PING packets).
$ tcpdump "icmp[0] != 8 and icmp[0] != 0"
TIME
TIME is the Time Protocol, defined by RFC 868. For a TCP connection, TIME returns a four-byte integer (in network byte order) of the current time in number of seconds since 1-JAN-1900 00:00 GMT. For UDP, when you receive a packet time port (37), TIME returns a four-byte datagram with the time (and discards the received datagram).
TRACEROUTE
This section describes the TRACEROUTE utility, which traces the path of an IP packet to an internet host. Only one user can run TRACEROUTE at a time. TRACEROUTE requires BYPASS or SYSPRV privileges.
Before using TRACEROUTE, enter the following to define the TRACEROUTE foreign command definition:
$ TRACEROUTE :== $TCPWARE:TRACEROUTE
To trace the path an IP packet follows to an internet host, enter the following format:
$ TRACEROUTE [-dnrv]
[-w wait] [-m max_ttl][-q nqueries]-
_$ [-t tos] [-s src_addr] host
|
-n |
Specifies to display internet addresses, not host names |
|
-r |
Specifies not to route (TRACEROUTE displays only directly "connected" hosts) |
|
-v |
Specifies verbose mode |
|
-wwait |
Is the number of seconds to wait between probes |
|
-m max_ttl |
Is the maximum time-to-live to set in or outgoing datagrams |
|
-q nqueries |
Is the number of probes sent |
|
-ttos |
Is the type of service (the default is 0) |
|
-s src_addr |
Is the source internet address to use (the default depends on the interface needed to reach the destination) |
|
host |
Is the name of the internet host whose path you want to trace |
Example 32-5 shows a TRACEROUTE command and the resulting output.
$ TRACEROUTE nic.ddn.mil
TRACEROUTE to nic.ddn.mil (192.112.36.5), 30 hops max, 38
byte packets
1 delta.nene.com (192.168.95.126) 0 ms 0 ms 0 ms
2 process-gw.nene.com (192.168.138.1) 0 ms 10 ms 0 ms
3 waltham-cr1.bbnplanet.net (131.192.148.49) 20 ms 0 ms 0 ms
4 cambridge2-cr3.bbnplanet.net (131.192.27.2) 10 ms 10 ms 10 ms
5 cambridge2-br1.bbnplanet.net (199.92.129.6) 10 ms 10 ms 10 ms
6 cambridge1-br2.bbnplanet.net (4.0.2.25) 10 ms 20 ms 10 ms
7 nyc1-br2.bbnplanet.net (4.0.1.121) 20 ms 30 ms 20 ms
8 nyc2-br2.bbnplanet.net (4.0.1.154) 30 ms 90 ms 120 ms
9 nynap.bbnplanet.net (4.0.1.26) 20 ms 40 ms 20 ms
10 niprnet.sprintnap.net (192.157.69.45) 420 ms 90 ms 90 ms
11 137.209.12.1 (137.209.12.1) 90 ms 90 ms 90 ms
12 * 198.26.119.26 (198.26.119.26) 90 ms 100 ms
13 nic.mil (192.112.36.5) 90 ms